Wildcard with Certbot and OVH
TL;DR further down the page
What?
A wildcard certificate is a single public key SSL certificate, enabling HTTPS on all your subdomains or aliases.
Cerbot is a tool to generate and renew free Let's Encrypt SSL certificates to ensure HTTPS on your website.
OVHcloud is a cloud computing company that offers VPS, dedicated servers and other web services.
Example
I do not own this domain and IP address, they are just used as an example
I have a domain name domain.io that points to my server :
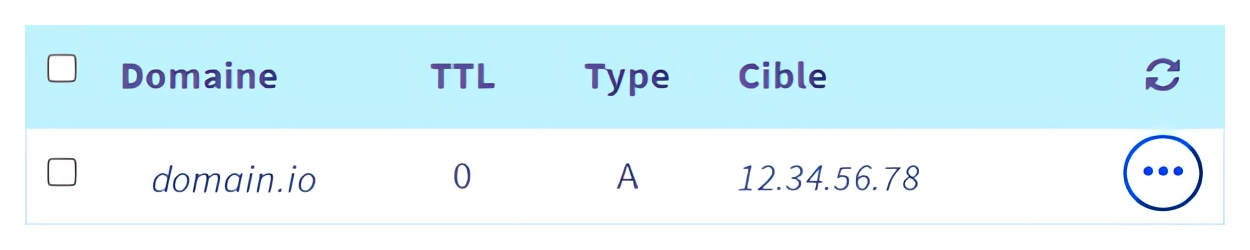
This server hosts three services behind a reverse-proxy, pointed by three aliases of domain.io :
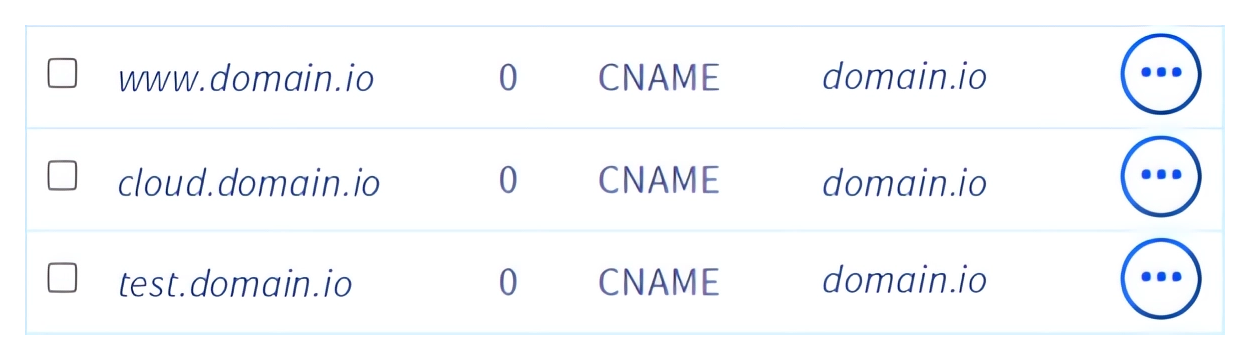
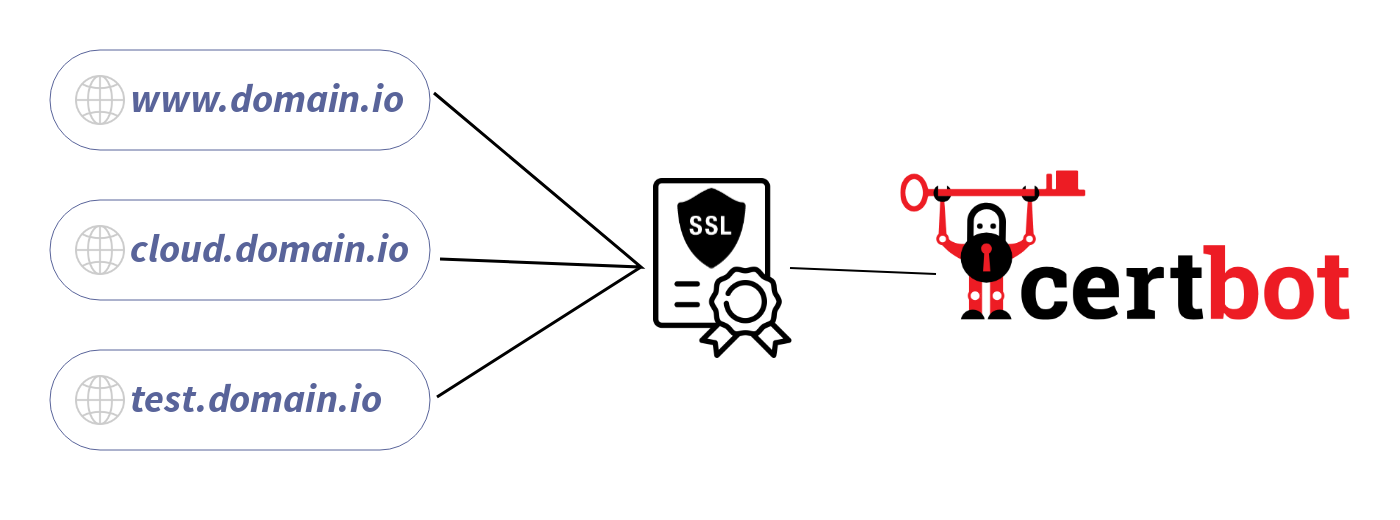
To use HTTPS on these services, I can generate three SSL certificates, one for each alias. The problem is that if I want to host more services, managing each one of them can become quite tricky. Imagine having to manage hundreds of certificates!

I can also generate a single certificate for those three services, but I will still need to generate a certificate every time I want to host a new service. Also, the certificate will list all my aliases, which I don't want for security reasons.
So instead, I can generate a single certificate, that will work with all recorded and future aliases : a Wildcard certificate
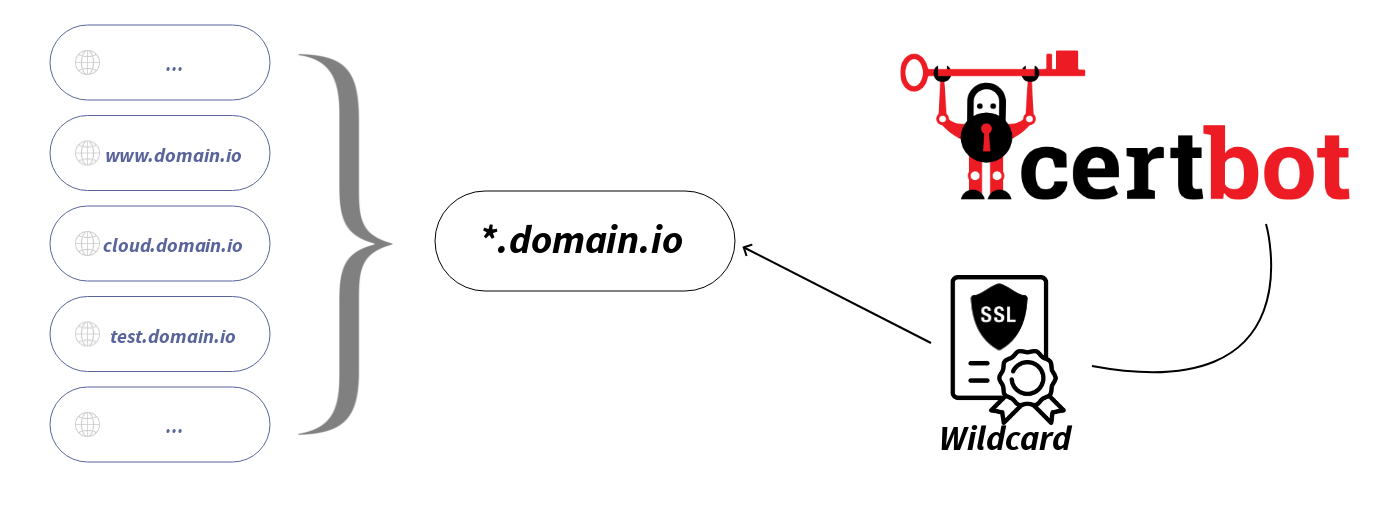
To proceed
Requirements
- An OVH domain name, pointing to your server
- certbot
- cerbot-dns-ovh
sudo apt install certbot python3 python3-pip
sudo pip3 install cerbot-dns-ovhGenerate API keys
- Login to https://eu.api.ovh.com/createToken/
Use your OVH user ID instead of your email (Looks like ab1234-ovh) - Fill the fields, and set all the right to
/domain/zone/*
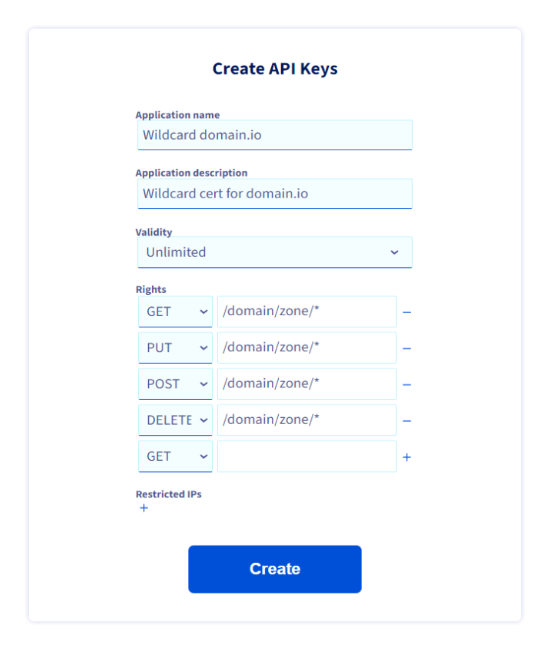
(!) Don't forget to add the last line (DELETE in this case) using its + button
- Write down in your password manager the generated API keys
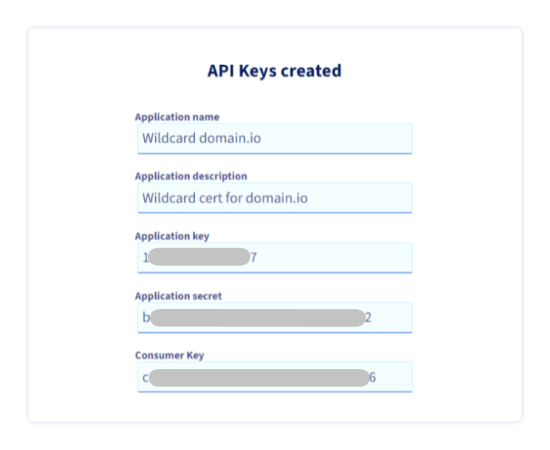
Check generated keys on API console (optional)
- Login to https://eu.api.ovh.com/console/#/me/api/application~GET
with your OVH user ID - Authorize console access: 1 hour is enough for a simple check
- Unroll "/me" (if not already done)
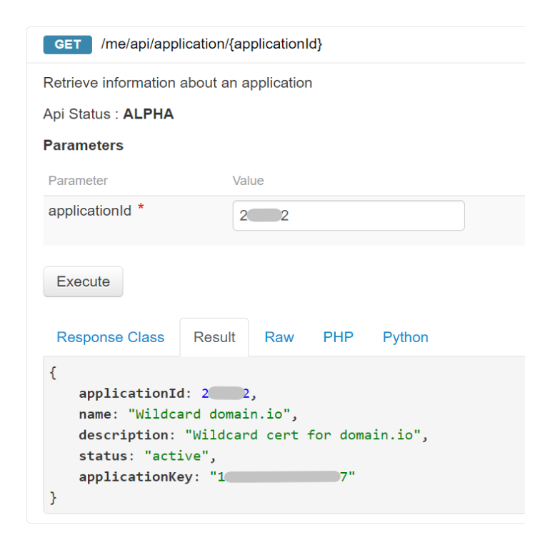
- Unroll GET /me/api/application
- Execute to display the application (API keys) ID generated previously
- Copy this ID - Now unroll GET /me/api/application/{applicationId}
- Paste the ID and Execute
- The result should display the application info (API keys)
DELETE /me/api/application/{applicationId}
Add the API keys on the server
On the host server :
- Create a restricted-access ovh.ini file
sudo mkdir -p /root/.secrets/cerbot/ && sudo touch /root/.secrets/certbot/ovh.inisudo chmod 600 /root/.secrets/certbot/ovh.ini- Edit the ovh.ini file with the previously generated API keys :
sudo nano /root/.secrets/certbot/ovh.ini
# OVH API credentials "Wildcard domaine.io"
dns_ovh_endpoint = ovh-eu
dns_ovh_application_key = MDAwMDAwMDAwMDAw
dns_ovh_application_secret = MDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAw
dns_ovh_consumer_key = MDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwCheck the configuration
Edit the following command, the --dry-run option is to test the configuration:
sudo certbot certonly -v --dry-run --dns-ovh --dns-ovh-credentials /root/.secrets/certbot/ovh.ini --non-interactive -d domain.com -d "*.domain.com" --agree-tos --email contact@domain.com --rsa-key-size 4096- Change the
-d domain.io -d "*.domain.io"parameters by your domain name
and the quotation marks " in the command line
- Change the
--email contact@domain.ioby yours
Generate the Wildcard certificate
Just remove the --dry-run option from your command
The Wildcard will be generated under /etc/letsencrypt/live/
--expand option in your commandMore options in the cerbot manual page :
cerbot -h or man-page certbotvHost SSL configuration
Here is a useful tool to help you generate an SSL vHost configuration file depending on your HTTP server and more (Apache, Nginx ...)
Restart and Test
Another tool to check your configuration

Automatic renewal
Since a free Let's Encrypt certificate last 3 months, you can add a Cron to automatically renew your wildcard : sudo crontab -e
# Certbot renew on even months
0 0 1 */2 * certbot renew && service nginx reloadTL;DR
Requirements :
sudo apt install certbot python3 python3-pip
sudo pip3 install cerbot-dns-ovhAPI keys : https://eu.api.ovh.com/createToken/
- GET, PUT, POST, DELETE =
/domain/zone/*
sudo mkdir -p /root/.secrets/cerbot/ && sudo touch /root/.secrets/cerbot/ovh.ini && sudo chmod 600 /root/.secrets/certbot/ovh.ini && sudo nano /root/.secrets/certbot/ovh.inidns_ovh_endpoint = ovh-eu
dns_ovh_application_key =
dns_ovh_application_secret =
dns_ovh_consumer_key = Generate Certs
sudo certbot certonly -v --dns-ovh --dns-ovh-credentials /root/.secrets/certbot/ovh.ini --non-interactive -d domain.com -d "*.domain.com" --agree-tos --email contact@domain.com --rsa-key-size 4096- To test :
--dry-run - To overwrite :
--expand
Index
- certbot (https://certbot.eff.org)
- man-page certbot (https://eff-certbot.readthedocs.io/en/stable/man/certbot.html)
- cerbot-dns-ovh (https://certbot-dns-ovh.readthedocs.io/en/stable/)
- Create OVH API Tokens (https://eu.api.ovh.com/createToken/)
- OVH Console API (https://eu.api.ovh.com/console/)
- SSL Labs (https://www.ssllabs.com/ssltest/index.html)





